This is an old revision of the document!
Enhance Plesk Security by Enabling TLS 1.3
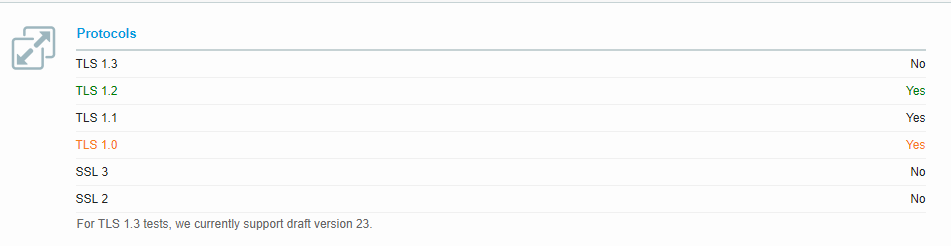
You can enhance Plesk's security features by enabling TLS 1.3 and disabling weak cipher suites.
By default, Plesk configuration enables TLS1.0 , TLS1.1 and TLS1.2. This guide will show you how to enable TLS 1.3.
This guide is made and tested on Plesk 17.8 and Centos 7.5. For Debian/Ubuntu Plesk ,configuration files should be located in /etc/apache2/mods-available/ssl.conf.
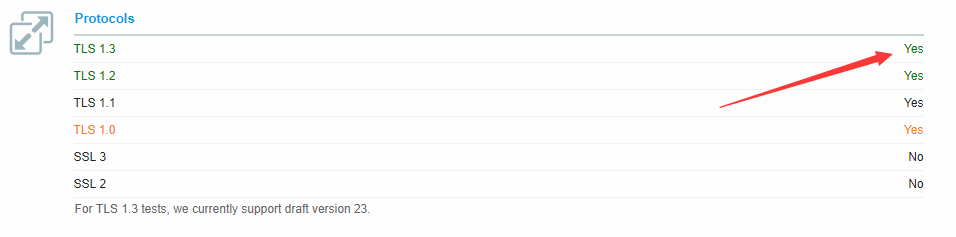
Enabling TLS1.3
Edit the file /etc/httpd/conf.d/ssl.conf.
Find the following line and comment out (you can use # ):
<IfModule mod_ssl.c> SSLProtocol +TLSv1 +TLSv1.1 +TLSv1.2 SSLCipherSuite HIGH:!aNULL:!MD5 </IfModule>
Replace it with:
<IfModule LiteSpeed> SSLProtocol TLSv1.1 TLSv1.2 TLSv1.3 SSLCipherSuite HIGH:!aNULL:!MD5 </IfModule>
This enables TLS1.1 , TLS1.2 and TLS1.3
If you want to disable TLS1.1 as well, then change the line to:
SSLProtocol TLSv1.2 TLSv1.3
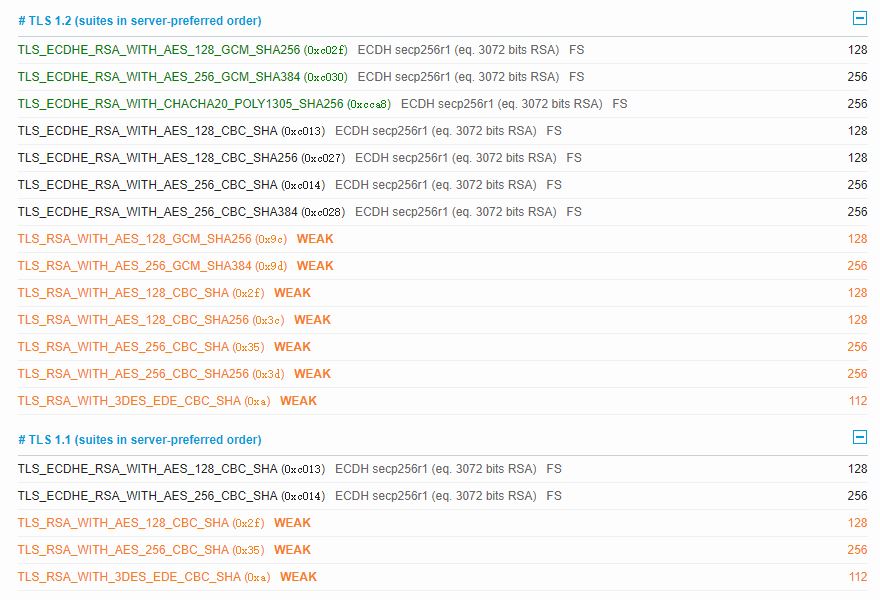
Disable Weak Cipher Suites (Optional)
By default, Plesk also comes with some weak cipher suites. If you want to disable them, find the following line:
SSLCipherSuite HIGH:!aNULL:!MD5
And replace it with:
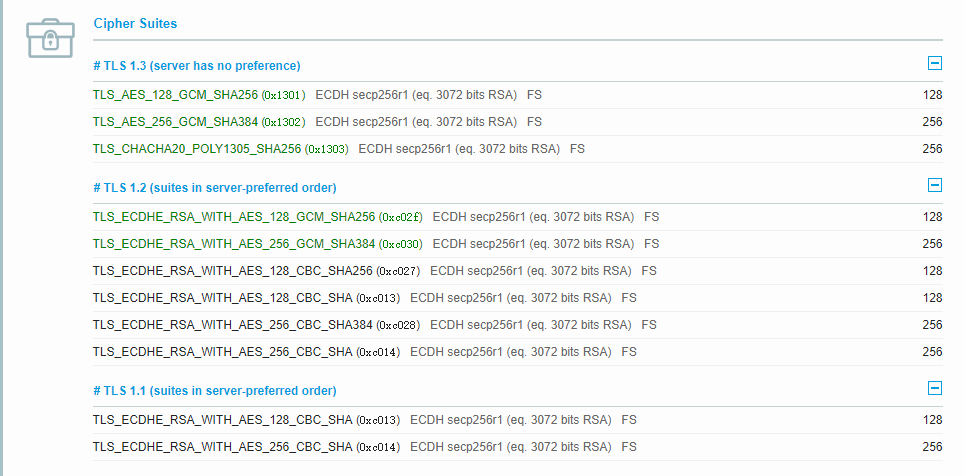
SSLCipherSuite TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256:TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384:TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256:TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA:TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384:TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA:TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA:TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
Be aware, this may cause CPU load.
Testing is done through SSL Lab.