This is an old revision of the document!
OCSP Stapling
Online Certificate Status Protocol (OCSP) was created as an alternative to the Certificate Revocation List (CRL) protocol. Both protocols are used to check whether an SSL Certificate has been revoked. The CRL protocol requires the browser to spend time downloading and then searching a list for certificate information. With OCSP, the browser simply posts a query and receives a response from an OCSP responder (a Certificate Authority’s (CA's) server that specifically listens for and responds to OCSP requests) about the revocation status of a certificate.
OCSP stapling can be used to enhance the OCSP protocol by letting the webhosting site be more proactive in improving the client (browsing) experience. OCSP stapling allows the certificate presenter (i.e. web server) to query the OCSP responder directly and then cache the response. This securely-cached response is then delivered with the TLS/SSL handshake via the Certificate Status Request extension response, ensuring that the browser gets the same response performance for the certificate status as it does for the website content.
LSWS version support
| LSWS Version | Through Apache config | LSWS native configure |
|---|---|---|
| 5.1+ | v | v |
| 4.2.x or 5.0.x | x | v |
| 4.2- | x | x |
Requirements
- Non-self-signed SSL Certificate
- Port 443 enabled for https
- If using Apache config, HTTPD Server 2.3.3+
Setup through Apache httpd.conf for 5.1.x and above
Follow the same method as Apache through httpd.conf. See these external references for more information: digicert.com or globalsign.com
For cPanel
Add the following lines to:
- For EA3:
/usr/local/apache/conf/includes/pre_main_global.conf - For EA4:
/etc/apache2/conf.d/includes/pre_main_global.conf
<IfModule Litespeed> SSLStaplingCache shmcb:/tmp/stapling_cache(128000) </IfModule>
Edit your site’s VirtualHost SSL configuration.
Add the following lines to:
- For EA3:
/usr/local/apache/conf/userdata/lscache_vhosts.conf - For EA4:
/etc/apache2/conf.d/userdata/lscache_vhosts.conf
(if these directories do not exist, create them).
<IfModule Litespeed> SSLUseStapling on </IfModule>
Apply these changes to all Virtual Hosts by running the following command:
/scripts/ensure_vhost_includes --all-users
Setup through LSWS native configuration for 4.2.x or 5.0.x
Set up a secure listener
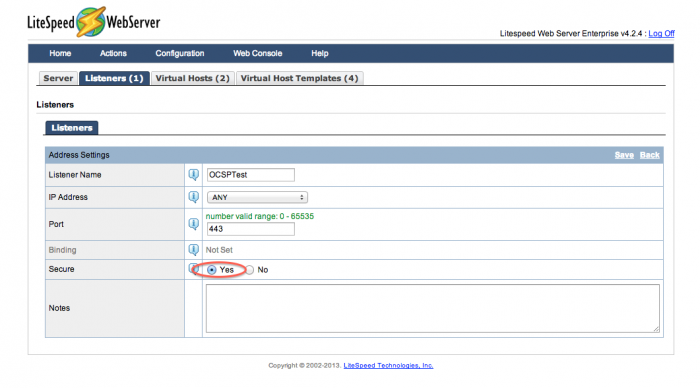
Add a listener (WebAdmin console > Configuration > Listeners > Add).
Make sure you click Yes under the Secure setting. (The other settings should be customized to listen to the correct IP and port for the virtual hosts this listener will be mapping to.)
Set up certificate files
Open up the listener again (View/Edit).
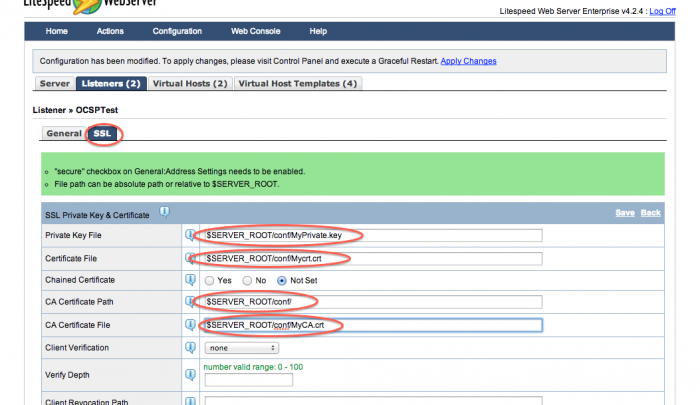
Under the SSL tab, enter the paths and locations for your certificates and key files.
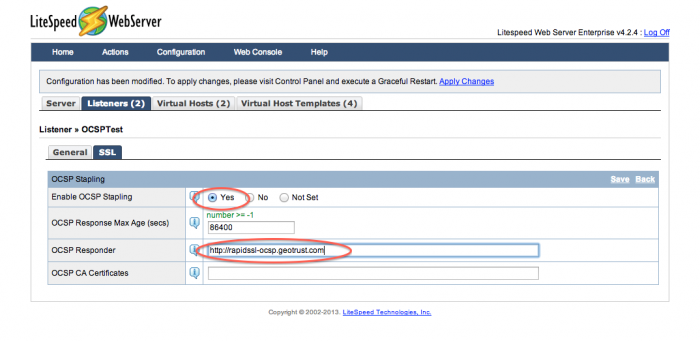
Set the OCSP values
To set up OCSP stapling, you must set Enable OCSP Stapling to Yes. It is also better to put the address of your OCSP responder in the OCSP Responder field (though the server may be able to find it in your CA certificate). Check with your CA for your OCSP responder's address.
Graceful restart
Click the Apply Changes link to execute a graceful restart and apply your changes.
Did it work?
Method 1:
Check in $SERVER_ROOT/temp/ocspcache/. If a file has been created there, then your OCSP stapling is working. If not, check your error logs for what went wrong.
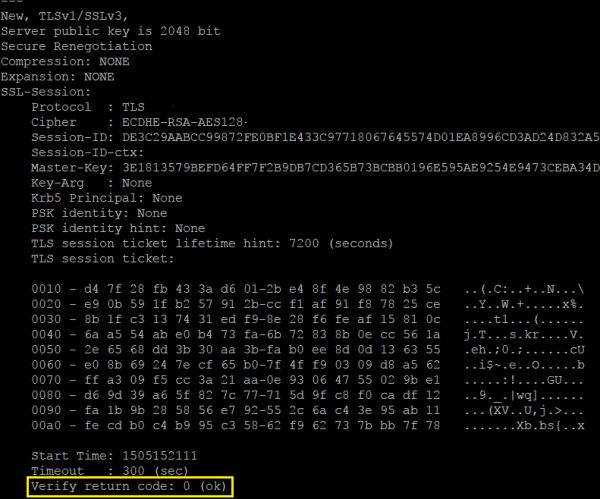
Method 2:
Use the openssl command:
openssl s_client -connect $Your_Domain:443 -status
If OCSP stapling is working, it will show ok. Then check OCSP Response Status: should be successful in OCSP Response Data section
Method 3:
- Open browser with URL
https://cryptoreport.rapidssl.com - key in your domain then check OCSP stapling status
Cached OSCP response
OCSP response is cached for 1-day. If you change your SSL certificate provider and see a cached OCSP response for a domain, you can easily remove the cache files under ocsp cache folder.