This is an old revision of the document!
How to install a SSL certificate on LSWS native mode?
On control panel environment, LSWS will read apache configuration. As far as you set SSL certificates correctly in apache config, LSWS should word as the same way as apache. While in LSWS native/OLS, you will need to set up SSL certificate settings in LSWS Web Admin configuration.
After you get the SSL certificate, either self signed or signed by a CA, you can configure your server to use the certificates. This wiki will explain to you all steps for such configurations.
Create 443 lister
Create a listener with Secure set to Yes. The official port for SSL is 443, but other port can be used as well.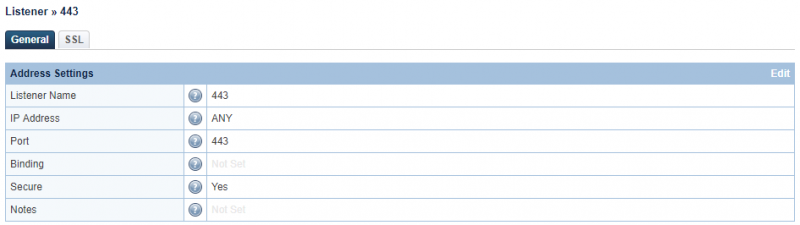
Setup SSL certificate
Self-signed certificate
Click on the newly created listener, then go to the SSL Settings. Then set the self-signed “Private Key File” and “Certificate File” to where the key file is. If you don't have the self-signed key pair yet, please follow here to create a private key and follow here to create a certificate.

CA certificate
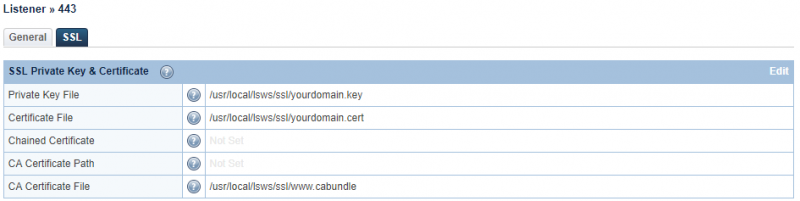
For a certificate signed by a certificate authority (CA), it comes either with intermediate certificates and your server/domain certificate. An intermediate CA certificate is a subordinate certificate issued by the trusted root specifically to issue end-entity server certificate separately or combined as chain certificate as the right order. The result is a trust-chain that begins at the trusted root CA, through the intermediate and finally ending with the SSL certificate issued to you. file or Chained certificate. An intermediate certificate is signed by one of the root certificates in a web browser, so your certificate will be trusted by a web browser because of the trust relationship among those certificates.
Intermediate certificates and server certificate separately
When you have separate intermediate certificates and server certificate, you can configure “Private Key File” and “Certificate File” to where the key file is and use either “CA Certificate Path” to define the location of multi intermediate certificates' location, or “CA Certificate File” to define the intermediate certificate if it is only one. “CA Certificate Path” and “CA Certificate File” are the equivalent setting and you just need to use one of them, but not both of them.
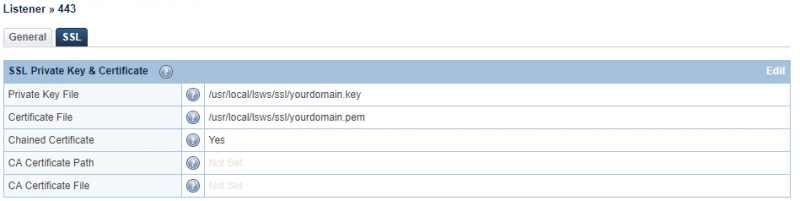
Chained certificate
If the certificate is a chained certificate, the file that stores a certificate chain must be in PEM format, and the certificates must be in the chained order, from the lowest level (the actual client or server certificate) to the highest level (root) CA
You can also combined separate tntermediate certificates and server certificate to a chained certificate yourself and set as above. for example: cat yourdomain.cert ca.cert > chained.pem
Testing
If you use a self-signed certificate, the browser will prompt you to accept the certificate, it is normal, if you use a certificate signed by a CA, the browser will accept the certificate automatically without bothering you.
Browser Testing
To test ssl certificates, visit your site https://yourdomain.com and you will see the green lock sign, which implies the https cert is working.
Online ssl checker
You can also use some online ssl checker to verify ssl certificates settings, such as https://www.ssllabs.com/ssltest/.
openssl command line
Alternatively, you can use Linux command line tool:
openssl s_client -connect example.com:443 -servername example.com
If the certificate is valid Verify return code: 0 (ok) line can be observed in the command output. To check the expiration date of the certificate run the following command:
# echo | openssl s_client -connect example.com:443 -servername example.com 2>/dev/null | openssl x509 -noout -dates notBefore=Feb 14 00:00:00 2017 GMT notAfter=Feb 14 23:59:59 2018 GMT