This is an old revision of the document!
How to use ConfigServer Security & Firewall (csf) together with LiteSpeed ADC for Anti-DDoS.
LiteSpeed ADC Anti-DDoS feature can modify firewall via ifconfig and ipset to block suspicious IP(s), and csf is commonly used firewall on many servers, this is guide for how to integrate LiteSpeed ADC's Anti-DDoS feature with csf.
LiteSpeed ADC configuration
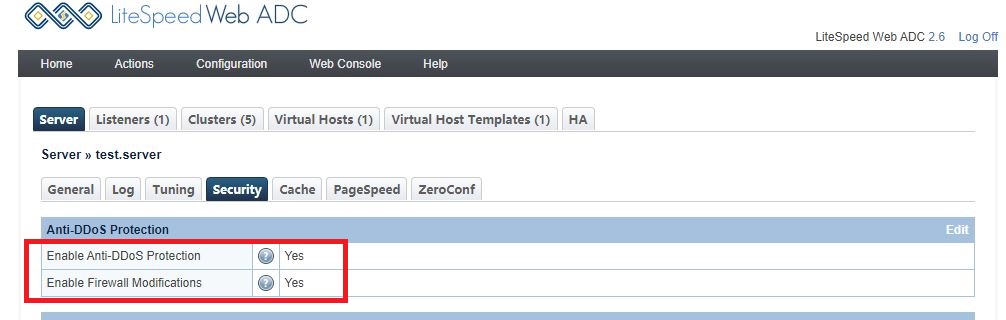
Login to ADC webadmin console by https://SERVER_IP:7090 , go to Configuration --> Security:
set Enable Anti-DDoS Protection and Enable Firewall Modifications to Yes to enable Anti-DDoS protection.
ConfigServer Security & Firewall configuration
create file /etc/csf/csfpost.sh with content:
#!/bin/bash ipset create ls-anti-ddos hash:ip hashsize 4096 ipset create ls-quic-ports bitmap:port range 0-65535 -exist iptables -I INPUT -m set --match-set ls-anti-ddos src -j DROP iptables -I FORWARD -m set --match-set ls-anti-ddos src -j DROP iptables -I INPUT -p udp -m set --match-set ls-quic-ports dst -j ACCEPT
and then reload it by command csf -r
verify if the script works as intent by checking with ipset list, now there should be 2 blocks ls-anti-ddos and ls-quic-ports
[root@test csf]# ipset list Name: chain_DENY Type: hash:net Revision: 3 Header: family inet hashsize 1024 maxelem 65536 Size in memory: 16784 References: 2 Members: Name: chain_ALLOW Type: hash:net Revision: 3 Header: family inet hashsize 1024 maxelem 65536 Size in memory: 16784 References: 2 Members: Name: ls-anti-ddos Type: hash:ip Revision: 1 Header: family inet hashsize 4096 maxelem 65536 Size in memory: 65680 References: 2 Members: Name: ls-quic-ports Type: bitmap:port Revision: 1 Header: range 0-65535 Size in memory: 524432 References: 1 Members:
Test
There are several cases the LiteSpeed ADC will consider an incoming request is suspicious , for example failed reCAPTCHA test or bad-formatted request.
For demonstration purpose , we will use reCAPTCHA failed verification to trigger the block.
So if visitor failed to verify many times in short time , it will trigger the firewall blocking , and there is also log like this
[root@test logs]# grep ipset error.log 2019-12-04 20:27:15.594490 [NOTICE] [24606] [T0] [FIREWALL] execute command: 'ipset add ls-anti-ddos 111.222.333.444 ', ret: -1, status: 0
and if run ipset list again , you will see content like this:
Name: ls-anti-ddos Type: hash:ip Revision: 1 Header: family inet hashsize 4096 maxelem 65536 Size in memory: 65696 References: 1 Members: 111.222.333.444
The IP will be removed from block in 10 minutes if it doesn't behave suspiciously anymore.
you should see log as this
2019-12-04 20:37:20.304327 [NOTICE] [24823] [T0] [FIREWALL] execute command: 'ipset del ls-anti-ddos 111.222.333.444 ', ret: -1, status: 0