This is an old revision of the document!
ConfigServer Security & Firewall and Iptables
LiteSpeed ADC's Anti-DDoS feature can be used to modify a firewall via ifconfig and ipset to block suspicious IPs. This guide explains how to integrate the ADC's Anti-DDoS feature with either ConfigServer Security & Firewall (csf), or iptables.
LiteSpeed ADC Configuration
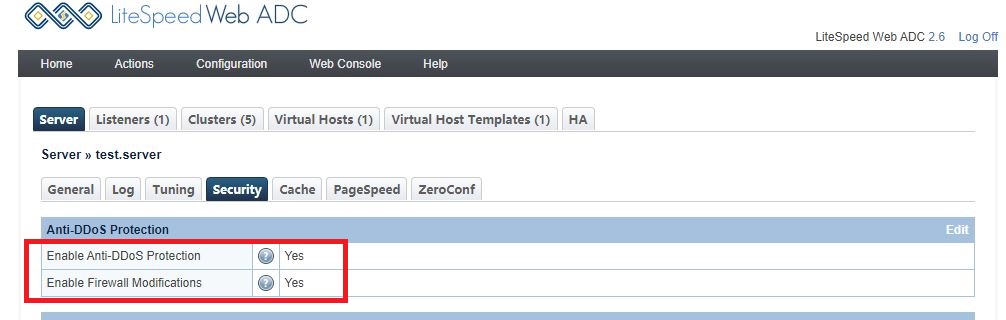
Log into the ADC WebAdmin Console at https://SERVER_IP:7090. navigate to Configuration > Security.
Set Enable Anti-DDoS Protection and Enable Firewall Modifications to Yes to enable Anti-DDoS protection.
ConfigServer Security & Firewall Configuration
For csf, create the file /etc/csf/csfpost.sh, and add the following content:
#!/bin/bash ipset create ls-anti-ddos hash:ip hashsize 4096 ipset create ls-quic-ports bitmap:port range 0-65535 -exist iptables -I INPUT -m set --match-set ls-anti-ddos src -j DROP iptables -I FORWARD -m set --match-set ls-anti-ddos src -j DROP iptables -I INPUT -p udp -m set --match-set ls-quic-ports dst -j ACCEPT
Reload with the command csf -r.
Iptables Configuration
For iptables, run the following commands to set up the list and rules:
ipset create ls-anti-ddos hash:ip hashsize 4096 ipset create ls-quic-ports bitmap:port range 0-65535 -exist iptables -I INPUT -m set --match-set ls-anti-ddos src -j DROP iptables -I FORWARD -m set --match-set ls-anti-ddos src -j DROP iptables -I INPUT -p udp -m set --match-set ls-quic-ports dst -j ACCEPT
Verify Ipset
Verify the script works as intended by checking with the ipset list command. You should see two blocks: ls-anti-ddos and ls-quic-ports.
[root@test]# ipset list ... ... Name: ls-anti-ddos Type: hash:ip Revision: 1 Header: family inet hashsize 4096 maxelem 65536 Size in memory: 65680 References: 2 Members: Name: ls-quic-ports Type: bitmap:port Revision: 1 Header: range 0-65535 Size in memory: 524432 References: 1 Members:
Test
There are several cases where LiteSpeed ADC will consider an incoming request suspicious. For example, a failed reCAPTCHA test, or a badly formatted request.
For demonstration purposes, we will use a reCAPTCHA failed verification to trigger the block. So, if a visitor fails to verify repeatedly in a short period of time, the firewall block will be triggered and a log generated, like this one:
[root@test logs]# grep ipset error.log 2019-12-04 20:27:15.594490 [NOTICE] [24606] [T0] [FIREWALL] execute command: 'ipset add ls-anti-ddos 111.222.333.444 ', ret: -1, status: 0
If you run ipset list again, you will see content like this:
Name: ls-anti-ddos Type: hash:ip Revision: 1 Header: family inet hashsize 4096 maxelem 65536 Size in memory: 65696 References: 1 Members: 111.222.333.444
The block on the IP will be removed in 10 minutes, if the suspicious behavior stops. At that point, you should see this in the log:
2019-12-04 20:37:20.304327 [NOTICE] [24823] [T0] [FIREWALL] execute command: 'ipset del ls-anti-ddos 111.222.333.444 ', ret: -1, status: 0