This is an old revision of the document!
WordPress Brute Force Attack Protection
A ‘brute force’ login attack is a type of attack against a website to gain access to the site by guessing the username and password, over and over again. WordPress is the most popular CMS and therefore it’s a frequent target of this type of attack. The wp-login.php and xmlrpc.php pages are the most common target of brute force attack by POST method. WordPress doesn’t have any built-in protection to prevent this, hence the need for a third-party solution.
Starting with version 2.1.2, LiteSpeed Web ADC has a built-in WordPress brute force attack protection system. It will protect shared hosting WordPress environments from large-scale brute force attacks, which have the potential to bring down entire servers.
How Brute Force Protection Works
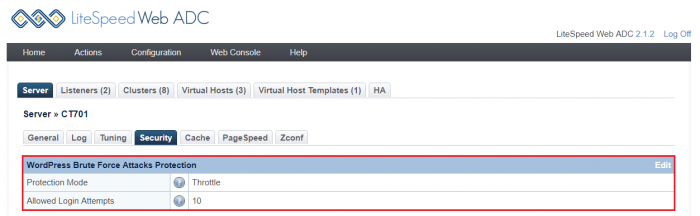
The newly introduced WordPress Protection directive is: [Throttle, Deny, Drop, Disable ]
The action is optional, and defaults to Disable. The Allowed Login Attempts can be set as value of (0|1|5-1000)
0disables WordPress Protection.1, when used by a virtual host, defers to the setting used by the server.5-1000enables WordPress protection and also specifies the login value. (Values lower than5will be treated as5, and values higher than1000will be treated as1000)
The Allowed Login Attempts value specifies the maximum number of wp-login.php and xmlrpc.php login attempts allowed within 5 minutes before the IP is blocked.
This Allowed Login Attempts is handled using a quota system that works as follows:
- The quota starts at the specified Allowed Login Attempts value.
- Each POST attempt decreases the quota by 1
- Once the quota reaches half of the value, the IP will be throttled, slowing more as the quota drops further.
- When the quota reaches 0, the desired action (drop, deny, or throttle) is taken.
- Over the course of 5 minutes without further POST attempts, the quota gradually increases back to the set
Allowed Login Attempts. - Restarting LSADC will reset the quota back to the specified value.
Examples
- Assume the
Allowed Login Attemptsis set to10. - When there are more than 5 attempts within a short period of time, the IP will be throttled.
- Once the quota reaches 0, the desired action (drop, deny, or throttle) will be taken.
- Every 30 seconds (5 minutes divided by the value = 30 seconds), if there are no further POST attempts, the quota will increase by 1.
- Assume the value is set to
300. - When there are more than 150 attempts within a short period of time, the IP will be throttled.
- Once the quota reaches 0, the desired action (drop, deny, or throttle) will be taken.
- After 1 second (5 minutes divided by the value = 1 second) without further POST attempts, the quota will increase by 1.
How to Enable LSADC WordPressProtect Feature from web console
The LSADC WordPressProtect feature is Disabled by default.
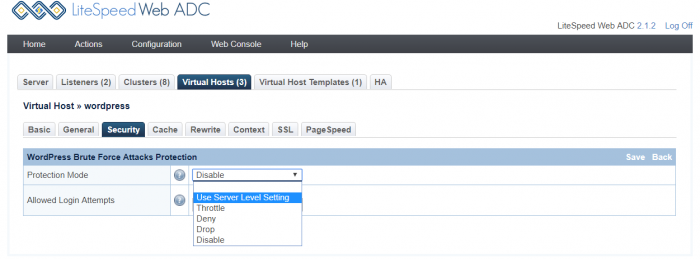
You may wish to override the default settings at the server level, virtual-host level. Before making any changes, it helps to understand the logic that drives WordPressProtect at the different levels.
Changing the settings at the Virtual-Host level configuration will override the Server-Level configuration.
The design logic looks like the following:
| Server Level | VHost Level | Result |
|---|---|---|
| not set | not set | X |
| 5 | not set | 5 |
| 5 | 10 | 10 |
| Disable | 10 | 10 |
Real Testing
Drop
This test was conducted with WordPressProtect set to drop 10. We can see the time start to increase at Round 6 and finally get a connection error at Round 10.
Round: 1
fail 0.291 status: 200
Round: 2
fail 0.256 status: 200
Round: 3
fail 0.256 status: 200
Round: 4
fail 0.279 status: 200
Round: 5
fail 0.249 status: 200
Round: 6
fail 1.275 status: 200
Round: 7
fail 2.287 status: 200
Round: 8
fail 3.267 status: 200
Round: 9
fail 4.271 status: 200
Round: 10
Erro MSG: ('Connection aborted.', RemoteDisconnected('Remote end closed connection without response',))
Deny
This test was conducted with WordPressProtect set to deny 10. We can see the time start to increase at Round 6 and start getting permission deny 403 status code from Round 10.
Round: 1 fail 0.292 status: 200 Round: 2 fail 0.267 status: 200 Round: 3 fail 0.270 status: 200 Round: 4 fail 0.253 status: 200 Round: 5 fail 0.268 status: 200 Round: 6 fail 1.257 status: 200 Round: 7 fail 2.276 status: 200 Round: 8 fail 3.260 status: 200 Round: 9 fail 4.182 status: 200 Round: 10 fail 1.010 status: 403
Log:
Brute force detected, deny
Throttle
This test was conducted with WordPressProtect set to throttle 10. We can see the time start to increase at Round 6 and start throttling from Round 10.
Round: 1 fail 0.289 status: 200 Round: 2 fail 0.269 status: 200 Round: 3 fail 0.268 status: 200 Round: 4 fail 0.243 status: 200 Round: 5 fail 0.263 status: 200 Round: 6 fail 1.269 status: 200 Round: 7 fail 2.266 status: 200 Round: 8 fail 3.280 status: 200 Round: 9 fail 4.182 status: 200 Round: 10 fail 29.249 status: 200
Log:
Brute force detected, throttle