This is an old revision of the document!
How to Setup Comodo on Standalone LiteSpeed Web Server
Comodo is a Mod_Security rule set created by the Comodo Team. It provides real time protection for web apps running on the LiteSpeed Web Server. Its functions include:
- Protecting sensitive customer data
- Meeting PCI compliance requirements
- Blocking unauthorized access
- Preventing SQL injection and Cross Site Scripting (XSS) attacks
The following wiki will explain how to enable the mod_security rule set on a LSWS native server. For a control panel environment, these steps are unnecessary. Simply enable the mod_security rule set from the control panel, the same way you would enable a rule set for Apache. For more information on that, please see this wiki.
Download and Extract Rules
We first need to download Comodo rules that are compatible with Litespeed.
cd /usr/local/lsws/conf wget https://waf.comodo.com/api/cpanel_litespeed_vendor unzip cpanel_litespeed_vendor cd comodo_litespeed/ mv rules.conf.main rules.conf
This will download Comodo Litespeed rules, and move rules.conf.main to rules.conf. This is the file we will reference in the WebAdmin console.
Add WAF Rule Set
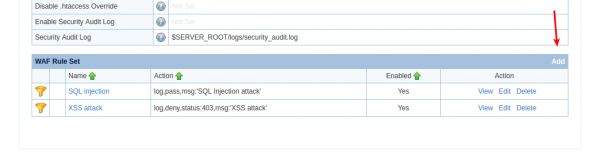
Navigate to Configurations » Server » Security » WAF Rule Set
Click Add to edit the WAF Rule Set
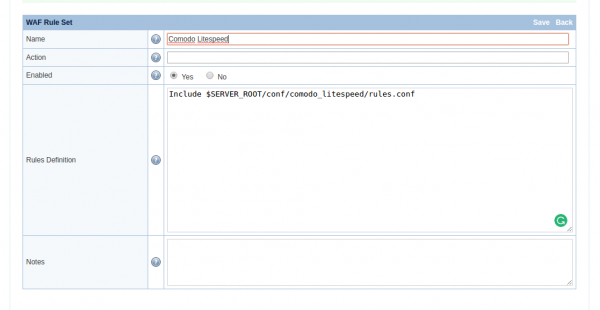
- Name:
Comodo Litespeed - Action:
None - Enabled:
Yes - Rules Defination:
Include $SERVER_ROOT/conf/comodo_litespeed/rules.conf
Click Save to activate the rules.
Enable Firewall
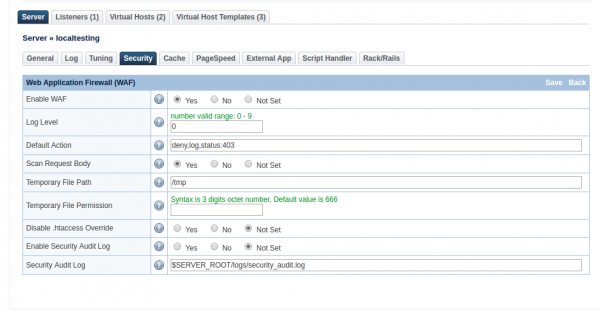
Navigate to Configurations » Server » Security » Web Application Firewall (WAF)
- Enable WAF:
Yes - Log Level:
0 - Default Action:
deny,log,status:403 - Scan Request Body:
Yes(If set toYeswill scan post request body) - Temporary File Path:
/tmp - Disable .htaccess Override:
Not Set - Enable Security Audit Log:
Not Set - Security Audit Log:
$SERVER_ROOT/logs/security_audit.log
Click Save to enable the firewall, and perform Graceful Restart.
Verify Comodo
Method 1
Method 2: Command injection attack
- Create a delete.php file with following codes
<?php print("Please specify the name of the file to delete"); print("<p>"); $file=$_GET['filename']; system("rm $file"); ?> - Create a dummy file
touch bob.txt
- Open
http://$server_domain/delete.php?filename=bob.txt;id
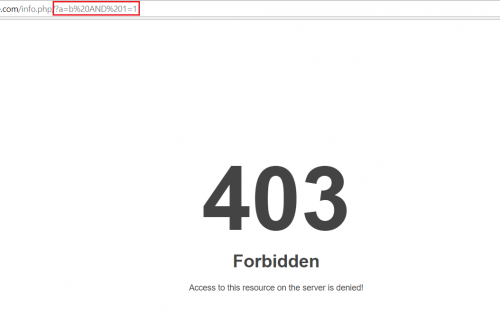
If WAF works, you will get a 403 forbidden page